11 | Add to Reading ListSource URL: www.cs.bham.ac.uk- Date: 2015-08-02 23:01:51
|
|---|
12 | Add to Reading ListSource URL: www.cs.columbia.edu- Date: 2012-06-11 10:18:08
|
|---|
13 | Add to Reading ListSource URL: www.cs.bham.ac.uk- Date: 2013-08-01 12:14:39
|
|---|
14 | Add to Reading ListSource URL: www.dsi.unive.it- Date: 2011-02-07 10:20:50
|
|---|
15 | Add to Reading ListSource URL: www.cs.bham.ac.uk- Date: 2013-08-01 12:14:38
|
|---|
16 | Add to Reading ListSource URL: www.pdl.cmu.edu- Date: 2014-01-28 13:54:50
|
|---|
17 | Add to Reading ListSource URL: cdn.batstrading.com- Date: 2016-08-09 02:52:02
|
|---|
18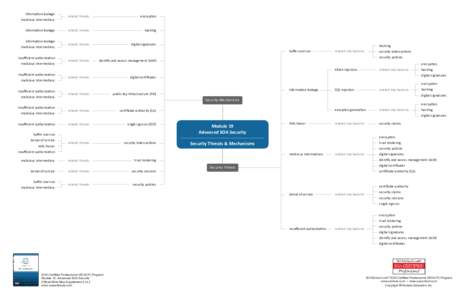 | Add to Reading ListSource URL: www.soaschool.comLanguage: English - Date: 2013-01-08 15:18:27
|
|---|
19 | Add to Reading ListSource URL: www.iaik.tugraz.atLanguage: English - Date: 2015-09-08 06:00:03
|
|---|
20 | Add to Reading ListSource URL: www.rsaconference.comLanguage: English - Date: 2015-04-23 11:43:47
|
|---|